Security Consulting Basics: A Guide for IT Professionals
- Carlos Perez Alviarez

- Aug 15
- 10 min read

Security consulting plays a huge role in keeping digital businesses protected. Cybercrime is getting more advanced every year, and organizations around the world face losses that exceed $8 trillion annually due to cyber attacks. Many people assume the solution is installing better firewalls or buying the newest software. That sounds logical at first, but the true edge comes from professionals who combine tech skills with sharp strategy and clear communication. Security consultants are the secret weapon most companies never see coming.
Table of Contents
Quick Summary
Takeaway | Explanation |
Security consultants protect digital assets | They help organizations defend against cyber threats and manage risks effectively. |
Develop key technical and analytical skills | Mastering network security, threat analysis, and problem-solving is crucial for success. |
Obtain relevant certifications for credibility | Credentials like CISSP and CEH demonstrate expertise and commitment in cybersecurity. |
Focus on continuous learning and networking | The cybersecurity field evolves rapidly; stay updated and connect with professionals for growth. |
Offer comprehensive security assessment services | Conduct thorough assessments to identify vulnerabilities and provide actionable recommendations for improvements. |
Understanding Security Consulting in IT
Security consulting in IT represents a critical field where professionals help organizations protect their digital infrastructure, sensitive data, and technological assets from increasingly sophisticated cyber threats. These specialized experts bridge the gap between technological complexity and strategic risk management, providing comprehensive guidance that goes beyond traditional IT support.
The Evolving Role of Security Consultants
Modern security consultants are strategic problem solvers who do more than simply identify vulnerabilities. According to NIST’s cybersecurity guidelines, they develop holistic risk management frameworks that enable organizations to proactively defend against potential security breaches. Their responsibilities encompass threat assessment, security architecture design, incident response planning, and continuous improvement of an organization’s defensive capabilities.
The landscape of cybersecurity is rapidly transforming, with consultants now required to understand complex interconnected systems, emerging technologies, and the nuanced threat environments across different industries. ISACA’s career insights highlight that successful security consultants must possess a multidisciplinary skill set that combines technical expertise, strategic thinking, and strong communication skills.
Key Competencies for Security Consulting Success
Effective security consultants must master a range of critical competencies. Technical skills form the foundation, including deep knowledge of network security, cloud infrastructure, encryption protocols, and vulnerability assessment techniques. Professionals need comprehensive understanding of technologies like firewalls, intrusion detection systems, and advanced threat protection mechanisms.
Beyond technical capabilities, security consultants must develop exceptional analytical and problem solving skills. They must translate complex technical risks into clear strategic recommendations that business leaders can understand and implement. This requires strong communication abilities, strategic thinking, and the capacity to explain technical concepts in accessible language.
Certifications play a crucial role in establishing credibility and demonstrating expertise. Professionals often pursue credentials like Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), and Certified Information Security Manager (CISM). These certifications validate a consultant’s knowledge and commitment to maintaining the highest standards of cybersecurity practice.
To help readers quickly compare some of the most recognized certifications for security consultants mentioned in this article, the following table summarizes key details about each credential and its focus area.
Certification | Abbreviation | Focus Area |
Certified Information Systems Security Professional | CISSP | Broad information security, risk management |
Certified Ethical Hacker | CEH | Ethical hacking, penetration testing |
Certified Information Security Manager | CISM | Information security management, governance |
CompTIA Security+ | Security+ | Entry-level security, foundational knowledge |
For IT professionals looking to transition into security consulting, our comprehensive guide on IT consulting careers provides detailed strategies for building a successful practice. Understanding the foundational principles of security consulting requires continuous learning, adaptability, and a proactive approach to addressing emerging technological challenges.
The demand for skilled security consultants continues to grow as organizations recognize the critical importance of robust cybersecurity strategies. By developing a comprehensive skill set that combines technical prowess, strategic insight, and effective communication, IT professionals can position themselves as invaluable assets in protecting digital infrastructures against increasingly sophisticated cyber threats.
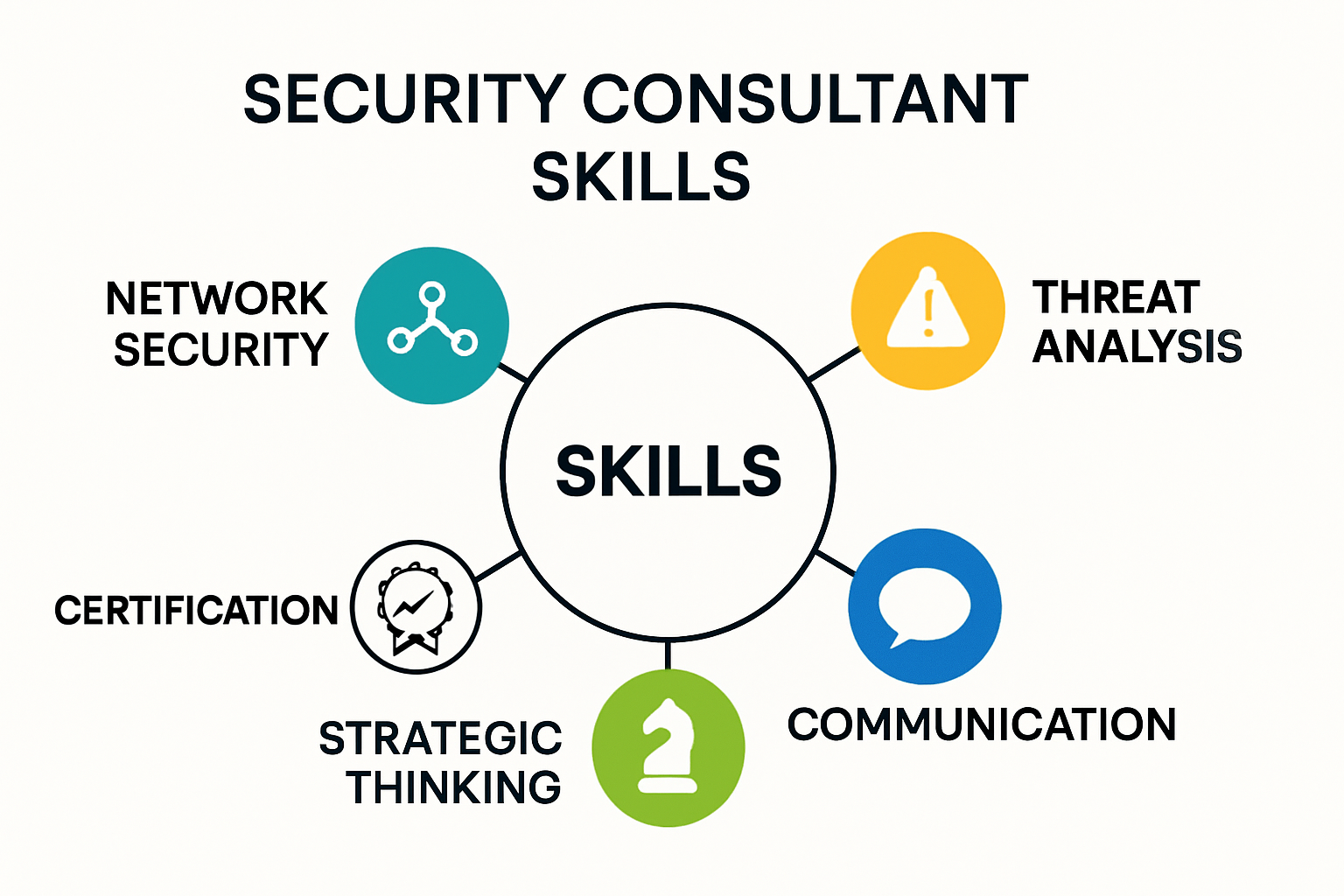
Essential Skills for Security Consultants
Security consulting demands a sophisticated blend of technical expertise, strategic thinking, and interpersonal capabilities that enable professionals to effectively protect organizations from complex cyber threats. These skills go far beyond traditional technical knowledge, requiring a holistic approach to cybersecurity risk management.
Technical Proficiencies and Specialized Knowledge
At the core of security consulting skills are robust technical competencies. According to Western Governors University, professionals must develop deep expertise in network security, penetration testing, firewall management, and advanced encryption techniques. This technical foundation requires proficiency in multiple programming languages, understanding of diverse operating systems, and the ability to conduct comprehensive vulnerability assessments.
Critical technical skills include advanced threat detection, incident response planning, cloud security architecture, and understanding of emerging technologies like artificial intelligence and machine learning in cybersecurity contexts. Consultants must stay current with rapidly evolving technological landscapes, continuously updating their knowledge to address emerging security challenges.
Analytical and Strategic Capabilities
CyberDegrees.org emphasizes that successful security consultants possess exceptional analytical and problem-solving skills. These professionals must transform complex technical vulnerabilities into strategic recommendations that business leaders can understand and implement. This requires the ability to assess risk holistically, anticipate potential security breaches, and develop proactive mitigation strategies.
Strategic thinking involves understanding the broader business context of cybersecurity. Consultants must align technical security recommendations with organizational goals, considering factors like business continuity, regulatory compliance, and potential financial implications of security incidents. Our comprehensive toolkit for IT professionals provides additional insights into developing these strategic capabilities.
Soft Skills and Professional Development
Beyond technical expertise, security consultants must cultivate strong communication and interpersonal skills. St. John’s University research highlights the importance of translating complex technical concepts into clear, accessible language for non-technical stakeholders. This requires exceptional verbal and written communication abilities, presentation skills, and the capacity to build trust with clients.
Professional development is crucial in this dynamic field. Security consultants must commit to continuous learning, pursuing advanced certifications like Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), and staying updated on the latest cybersecurity trends and technologies. Networking, attending industry conferences, and participating in professional communities are essential strategies for maintaining cutting-edge expertise.
The most successful security consultants combine deep technical knowledge with strategic insight, strong communication skills, and an unwavering commitment to protecting organizational assets. By developing a comprehensive skill set that addresses both technical and interpersonal dimensions of cybersecurity, professionals can establish themselves as invaluable strategic partners in an increasingly complex digital landscape.
Common Security Consulting Services
Security consulting encompasses a diverse range of services designed to help organizations identify, assess, and mitigate cybersecurity risks across their technological infrastructure. These specialized services provide comprehensive protection strategies tailored to unique organizational needs and technological environments.
To clarify the range of security consulting services described in the article, the table below organizes these core offerings and provides a brief explanation for each, helping readers quickly scan the service landscape.
Service Type | Description |
Security Assessment & Risk Management | Conducts vulnerability scanning, penetration testing, and comprehensive threat modeling |
Compliance & Regulatory Advisory | Helps organizations meet standards like GDPR, HIPAA, PCI DSS, and NIST; develops governance |
Security Architecture & Implementation | Designs and implements security frameworks, cloud, and network security solutions |
Employee Training & Awareness | Develops training modules to educate staff on security best practices and protocols |
Comprehensive Security Assessment and Risk Management
At the core of security consulting services are comprehensive security assessments that provide organizations with a holistic view of their cybersecurity posture. According to the University of Colorado’s Information Security Office, these assessments involve detailed reviews of existing security architectures, technological infrastructure, and potential vulnerabilities.
Security consultants conduct thorough risk assessments that include vulnerability scanning, penetration testing, and comprehensive threat modeling. These evaluations help organizations understand their specific security risks, identifying potential weaknesses in network configurations, access controls, and data protection mechanisms. Consultants provide actionable recommendations that enable organizations to prioritize and address critical security gaps effectively.
Compliance and Regulatory Advisory Services
Harvard T.H. Chan School of Public Health’s Information Security Team highlights the critical importance of compliance consulting in today’s complex regulatory environment. Security consultants help organizations navigate intricate regulatory landscapes, ensuring adherence to industry-specific standards like GDPR, HIPAA, PCI DSS, and NIST frameworks.
Compliance services include comprehensive reviews of data handling practices, security policy development, and implementation of robust governance frameworks. Consultants assist organizations in developing comprehensive data protection strategies, conducting privacy impact assessments, and creating documentation that demonstrates regulatory compliance. Learn more about developing robust consulting contracts to effectively communicate these complex advisory services.
Strategic Security Architecture and Implementation
Beyond assessment and compliance, security consultants provide strategic guidance in designing and implementing advanced security architectures. This involves developing comprehensive security frameworks that integrate seamlessly with existing technological infrastructure, addressing both current and emerging cybersecurity challenges.
Key implementation services include cloud security design, secure network architecture development, endpoint protection strategies, and advanced threat detection system configuration. Consultants help organizations select, implement, and optimize security technologies, ensuring that technological solutions align with broader business objectives and risk management strategies.
Implementation services also encompass employee training and awareness programs, recognizing that human factors are often the most significant vulnerability in cybersecurity systems. Consultants develop tailored training modules that educate staff about potential security risks, best practices, and organizational security protocols.

The most effective security consulting services provide a comprehensive, strategic approach that goes beyond technical solutions. By combining deep technical expertise, strategic insight, and a thorough understanding of organizational dynamics, security consultants help businesses build resilient, adaptive cybersecurity capabilities that protect against evolving digital threats.
Starting a Career in Security Consulting
Transitioning into security consulting requires a strategic approach that combines educational preparation, technical skill development, and professional networking. IT professionals looking to enter this dynamic field must develop a comprehensive strategy that positions them as valuable cybersecurity experts.
Educational and Certification Foundations
ISACA’s career guidance emphasizes the critical importance of formal education and professional certifications in establishing credibility within the security consulting landscape. Most employers require at least an undergraduate degree in computer science, cybersecurity, information technology, or a related technical field. This foundational education provides the theoretical knowledge necessary to understand complex security frameworks and technological infrastructures.
Professional certifications play a pivotal role in demonstrating expertise and commitment to the field. Key certifications for aspiring security consultants include Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), CompTIA Security+, and Certified Information Security Manager (CISM). These credentials validate technical skills and demonstrate a comprehensive understanding of cybersecurity principles, risk management, and security architecture.
Developing Practical Experience and Technical Skills
CompTIA’s career insights highlight the importance of gaining practical experience through diverse technical roles. Aspiring security consultants should seek opportunities in network administration, security analysis, incident response, and system vulnerability testing. These positions provide hands-on experience in identifying and mitigating security risks, developing critical problem-solving skills essential for consulting work.
Technical skill development involves mastering multiple programming languages, understanding complex network architectures, and staying current with emerging cybersecurity technologies. Professionals should focus on developing expertise in areas such as cloud security, threat intelligence, penetration testing, and advanced security tool implementation. Learn more about transitioning to consulting roles to understand the comprehensive skill development process.
Professional Networking and Career Strategy
The University of Tulsa’s career guidance emphasizes the significance of strategic professional networking and continuous learning. Attending industry conferences, participating in cybersecurity forums, and connecting with experienced security professionals can provide invaluable insights and potential career opportunities.
Building a professional portfolio that showcases practical project experience, successful security implementations, and demonstrable problem-solving skills is crucial. This might include documenting vulnerability assessments, security architecture designs, and incident response strategies. Many professionals also benefit from contributing to open-source security projects, writing technical blogs, or presenting at industry conferences to establish thought leadership.
Successful security consultants recognize that their career is a continuous learning journey. The cybersecurity landscape evolves rapidly, requiring professionals to invest consistently in skill development, stay informed about emerging threats, and maintain a proactive approach to professional growth. By combining rigorous technical training, practical experience, professional certifications, and strategic networking, IT professionals can effectively launch and advance their careers in security consulting.
Frequently Asked Questions
What is security consulting in IT?
Security consulting in IT involves experts helping organizations safeguard their digital infrastructure and sensitive data from cyber threats. They provide strategic guidance, risk management frameworks, and recommendations for improving cybersecurity.
What are the essential skills needed for a career in security consulting?
Key skills include technical proficiencies in network security and encryption, analytical abilities for risk assessment, and strong communication skills to effectively relay complex concepts to stakeholders.
What common services do security consultants offer?
Common services include comprehensive security assessments, compliance and regulatory advisory, strategic security architecture and implementation, and employee training on security best practices.
How can one start a career in security consulting?
To begin a career in security consulting, obtain relevant education in computer science or cybersecurity, pursue professional certifications like CISSP or CEH, gain hands-on experience in related roles, and develop a professional network in the industry.
Ready to Turn Your Security Expertise into a Fulfilling Solo Consulting Career?
You have just learned the fundamentals of security consulting, including how to assess risks, build strategic security frameworks, and navigate compliance challenges. The big question many IT professionals face now is how to move beyond the technical work and launch a thriving consulting business of their own. If you find yourself overwhelmed by career uncertainty, or unsure how to transform your cybersecurity skills into consistent income, you are not alone. The desire for freedom, income, and control is real—and so is the fear of missteps and wasted effort.
Let The Consultant’s Compass guide your next move. Explore our proven resources and get direct mentorship from Carlos E. Perez Alviarez, a consultant with over 13 years of solo success. Download the bestselling Becoming a Solo Consultant guide and unlock your smooth transition into consulting. Take your security consulting skills from theory to profit—visit https://consultantcompass.ca now and start building a business where your expertise stands out for clients who need you most.
Recommended








Comments